Computer has been locked by CryptoLocker virus ransomware, your personal files are encrypted and you have unfortunately “lost” all your pictures, files and documents on the computer? How to recover encrypted files without paying 300 USD or 100 EUR or 2 Bitcoins? Do people need to get the private key by paying a certain amount of fine to get all the files back? Is there any way to verify this pop-up block screen? I just got this CryptoLocker virus and it locks down your computer with a random password and my screen goes blank after starting. I can’t see the start button not even in safe mode. I just tried the listed removal method it goes to the same blank scree. Can I please get some help? How to get rid of this unwanted screen and decrypt all the files from this CryptoLocker program?
CryptoLocker Virus Locked Computer And Your personal files are encrypted – How to Fix The Problems?
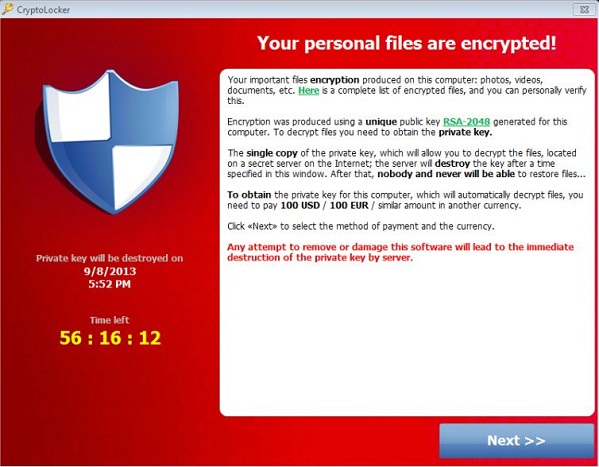
CryptoLocker Virus (also known as Crypto Locker Virus) is a new ransomware that affects files like photos, music, videos, documents, and so on. All Image, Video, MS office, PDF files are encrypted. This CryptoLocker Your personal files are encrypted Virus is viewed as a rather risky ransomware which has just been released to attack computers. This big virus has infected a number of computers all around the world, and the suffering centre is the Unites States of America, so the majority of the victims is Americans. This CryptoLocker virus can not only lock up browsers but also block the whole computers sometimes. After being infected by this virus, the only thing that jumps into your sight is a red blocking screen message stating that all the files on your PC including videos, photos and documents have been encrypted, and you are required to pay an amount of $100 or 100 euro to access a private key in order to have these encrypt files recovered. You can’t close this CryptoLocker virus locked screen no matter how many times you have tried. Even though you may get the task manager window open by pressing ctrl+shift+esc three keys together, ending the processes in task manager won’t be helpful at all.
In most cases, computer users have no idea when the virus has been installed and why they get this CryptoLocker Your personal files are encrypted virus message because the ransomware doesn’t need approvals from PC users to get its application installed. Downloading and installing unknown programs from the Internet, clicking links or visiting sites randomly can often be the reasons for causing this computer infection because we don’t know if the links or programs contain something that is as malicious as this CryptoLocker virus. By bundling with those free programs, processes and spam E-mail attachments, the virus can sneak into different computers without permissions and get activated later on. Therefore we need to behave ourselves accordingly when surfing the Internet, and be cautious as much as we can in order to stay away from this upsetting infection.
When having this CryptoLocker virus screen popped up on computer, you will read that “CryptoLocker Your personal files are encrypted!”. Because of this encryption, you won’t be able to access personal files on the computer. According to this virus message, you will need to get a private key by paying 100 USD or 100 EUR within the required time period. Once the time elapses and you haven’t been able to pay, the private key will be automatically destroyed on the server with a count-down time table on the left side of the page to force you to pay ASAP. Also, if you try to remove or damage this CryptoLocker program, the private key will be destroyed permanently as well. Trying to scare innocent PC users as possible as it can, this CryptoLocker virus can help cyber criminals benefit instead.
CryptoLocker virus is extremely dangerous computer Trojan infection which has been released by cyber hackers in September 2013. It belongs to a ransomware program which can attack all the machines with Windows operating systems, including Window XP, Windows Vista, Windows 7 and 8. Being different to other computer viruses and Trojan, this computer virus has a specific target group; people who live in USA become the most vulnerable aimed for this virus, and people who live in elsewhere all over the world are barely reported about being infected by this CryptoLocker. You have to get it fixed ASAP.
To save your computer, Live Chat with YooSecurity Expert Now. You can follow the manual removal guide below to get your problem fixed. (For advanced computer users)
Screenshot of CryptoLocker Virus Your personal files are encrypted!
What Will You Do If Your Computer Has Been Infected With CryptoLocker Virus Ransomware
This CryptoLocker can infect computers in various ways, this virus can pretend as a legit E-mail attachment to attract unwitting people to download, especially the E-mail content can be phony tracking notifications from FedEx and UPS or other formal business messages. Usually, those fake E-mails are sent from some places in the names of companies. Actually, those companies are all counterfeit by cyber hackers who want to cheat the victim to open the malicious E-mail and download the attachment willingly. To be more specific, the vicious attachment can be a ZIP file for people to download, once people finish the download and extract the file, a fake PDF or music file can be display to the people, but actually, the real extension for this file is .EXE which is an installation file for this CryptoLocker. Hackers can take the advantage of the Windows default setting about hiding the extension for known file types, and EXE can be one of them for computer to recognize. Also the file icon can be pretended as a PDF picture, which can be more confused to mislead innocent people to open.
Once people click on the fake attachment, this CryptoLocker virus ransomware can be activated in no second. Once it is installed in the infected computer, a folder with random name can be created in the Documents and Settings, and the computer registry can be out of the order. The Windows registry is a hierarchical database which stores configuration settings and options on Microsoft Windows operating systems, once this registry is messed up by this CryptoLocker, computer can perform improperly. Also, this ransomware can add its own key to the registry so that it can run on the startup. This CryptoLocker can do a full scan on the physical drives and mapped network drives in the infected computer, and then encrypts those data files which can be recognized by this infection, for example, the files with following extensions can be encrypted by this infection, *.doc, *.docx, *.jpg, *.xls and so on, from Microsoft Office documents to AutoCAD files, this infection can almost encrypt all kinds of files which are saved in the infected computer. This infection can connect one of the several specific command and control servers which are created by cyber criminals. Once connected, the server will generate a key pair which calculated with 2048-bit RSA and then send the key back to the infected computer to encrypt the files which make it difficult for the computer user or even expert to break. Police can use the specific IP address to trace the location of the servers, but cyber hackers change the servers which host the CryptoLocker virus frequently to hide their tracks. From the report by the police, hackers rarely remain the CryptoLocker virus on the same server for more than a week, and the servers can be changed from one continent to another one. In this case, it is really difficult to catch the cyber hackers who host this virus.
Once this CryptoLocker virus finishes the encryption on the infected computer, it can displays a warning message to computer user claiming that files have been encrypted, and in order to get the files back to normal, PC user is asked to pay $300 through an anonymous pre-paid cash voucher like MoneyPack or Ukash to decrypt the files. Also, the message tells the victim to pay within 72 hours, if not, the files which are encrypted can be destroyed automatically, and the PC user will never get them back. And it also claims that once the payment is done, the victim will receive the decryption key to decrypt the files or the files can be automatically decrypted by the server. However, from the victim reports on the Internet, some victims who pay the attackers but their files are still encrypted.
For those people who suffer from this CryptoLocker virus, please do not pay for this virus and do not hesitate to remove this virus as soon as you detect that your computer is infected by this computer threat. Only in this way, you can avoid more damage and loss.
Most of the people would pay the fine because of scare of government. However, the computer still locked by the CryptoLocker Virus when you finished payment. The worst thing is, you will never get your money back, and the situation can get worse. The CryptoLocker Your personal files are encrypted virus is actually a cyber fraud that the virus creators set for innocent computer users mostly from the United States to deceive their money. One should never ever believe or even pay a dollar or euro to this big scam. Or you will regret right after finishing the payment since a private key will not be given to decrypt all your “lost” files. The scam is not that easy to get rid of. Is there any way to un-encrypt files affected by cryptolocker virus? The virus is removed from my desktop but hundreds of documents are encrypted / corrupted. Effective and quick steps to remove the virus and get all your files back will be listed in the following passages.
Manual Removal Step by Step Instructions
Since system failed to boot normally and comes to this Virus screen, try to boot the computer into safe mode. To achieve that, you need to keep hitting F8 key, where is the key?(This is just for Windows XP, Windows Vista and Windows 7, if the OS is Windows 8, click here for more details)

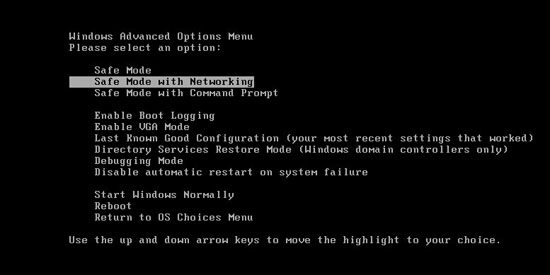
Step A: Restart your infected computer to safe mode with networking. You need to press Ctrl+Alt+Delete keys together to select Log off or Shut down at first, then press the power button to boot the computer up again; repeatedly and constantly keep hitting F8 key until you can see three safe mode options on a black screen including safe mode, safe mode with networking and safe mode with command prompt; use arrow keys to highlight safe mode with networking and hit Enter key. When the log in screen comes up, please log in the infected user account. A black desktop with safe modes at all corners will be shown. Usually, the CryptoLocker virus will not activate in this mode. Then we can move on to the next steps:
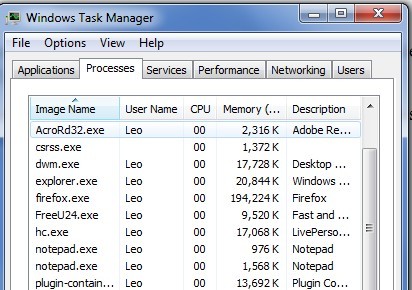
Step B: Press Ctrl+Alt+Del keys to open the Windows Task manager to stop the processes associating with CryptoLocker virus. Because the name will be changed fast, it will be shown with different names:
Step C: Delete all the files related to CryptoLocker Virus Ransomware:
%Temp%\random
%appdata%\random
%StartupFolder%\random.lnk
Step D: Delete registry entries of this infection created in computer system:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\run\random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System “DisableRegedit” = “”.exe.dll
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Settings\{random.exe}
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun=””
Video Guide to Remove This Scam Virus
Alternatively, you can view this CryptoLocker Virus scam removal video guide directly on our website.
Conclusion
Although CryptoLocker virus is ransomware, it’s not acting like other members from the same category that pretend to be legit government blocks and ask for ransom to unlock your computer. Instead, it pops up saying Your personal files are encrypted. It even threatens you that if payment is failed to enter, you will not be able to access your files permanently because the private key to decrypt files will be destroyed within a certain time period. Besides, the virus can display numerous fake infections on your computer trying to make you scared. And it also has the ability to steal your confidential information since it usually bundles with Trojan viruses and keyloggers etc. To conclude, CryptoLocker is a tricky ransomware made by cyber criminals aiming at making illegal profits from innocent PC users. Don’t be fooled that the virus will decrypt your personal files after the payment. One thing you should keep in mind is that this infection is only a cyber fraud. So, please ignore the warnings that shown on your PC screen and try to unlock PC from this CryptoLocker Your personal files are encrypted virus.
Special tips: Still failed to remove this CryptoLocker virus? By starting an online chat session, you will get immediate help from YooCare online PC experts who are specializing in virus removals to remove the nasty ransomware once for all:
Published by Tony Shepherd & last updated on April 10, 2014 3:44 am










Leave a Reply
You must be logged in to post a comment.