Has your computer suddenly been locked by a warning page from Information Security and Control Act (ISCA) 2012? Do you have any idea of why it locks your computer? Or have you really done the activities it states you have? Is it real and legit? If I don’t pay, would I be in trouble with any legal issues? Most importantly, how do I get my computer work again?
ISCA 2012 Description:
Information Security and Control Act (ISCA) 2012 is categorized as one of the newly released programs by hackers in order to collect as much money as possible from innocent computer users worldwide. How does it achieve that? By locking your computer in the names of nation and government and threatening to you with legal issues, it requests certain amount of fine from you to automatically unlock your computer. And the fine should be paid within the required period of time. Otherwise, you will be in troubles with legal issues. But no matter how legit this malware looks, it’s not real! If you still feel doubtful about this fact, please do some researches online or call local police or related organizations to confirm whether it’s legit or not. But before you are 100% certain, do not pay for it hoping to unlock your computer!
Reasons for you to be blocked by this ISCA 2012 virus do not totally match with its statements. Normally, this kind of malware, like International Police Association (I.P.A) scam or Police Cybercrime Investigation Department Malware, will state that your certain online activities have been violating the Law of Copyright or Related rights Law. You may have visited pornographic contents online to cause this blocking. But that’s just what it states you have done. You know better than anyone else of what you have done. Even if you do have accidentally open some porn sites, you cannot be hunted down and blocked by police through your IP address. The only reason this malware statement says so is because everyone is feared of legal issues, hence the paying chances are higher. But what would happen once you pay the fine? According to the locking screen of Information Security and Control Act (ISCA) 2012, it promises that your computer will be automatically unlocked within the next 72 hours. Then what would happen after 72 hours if you don’t pay? Your computer will still be locked and there will not be a policeman knocking at your door to hand you court paper. But still, this malware should be removed as soon as possible. More problems will happen if you leave it stay long inside your computer.
To save your computer, Live Chat with YooSecurity Online Expert now, or you can follow the manual removal guide below to get your problem fixed. (For advanced computer users)
Information Security and Control Act (ISCA) 2012 Screenshot:
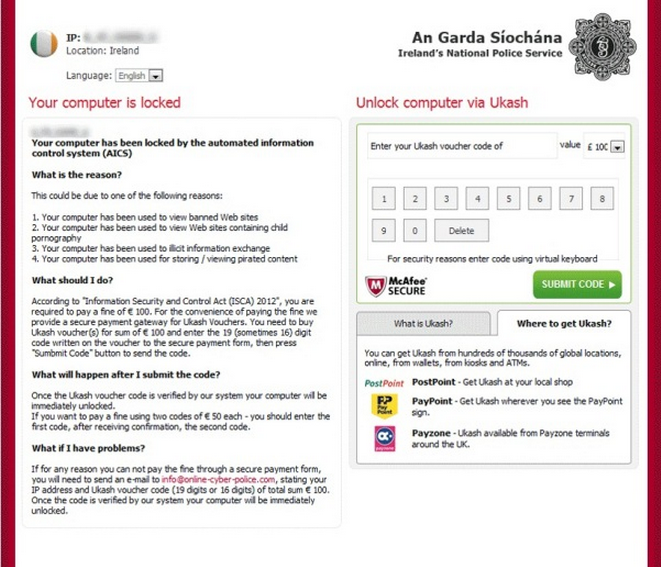
How Do I Remove Information Security and Control Act Virus?
Is there any better software to download to remove this Information Security and Control Act (ISCA) 2012 malware? The answer is NO. First of all, hackers know well how computer and antivirus software work, and in order to collect money, they will enable this malicious program to sneak into your computer without permission. In other words, if this malware can be easily caught by antivirus programs, it cannot help hackers to achieve their goals. Second of all, a program may be able to get off the locking screen but cannot completely remove the virus. It takes time for PC protection tools to upgrade and make better solutions while it takes minutes or hours to create another virus or malware. Then would reinstall system work? It’s not 100% guaranteed and it takes much time. Besides, reinstall system too often may damage the performance of hard disks. To manually remove this virus, you just need to uninstall it from the root and delete infected or fake files and registry entries.
How to Remove Fake ISCA 2012 Ransomware Efficiently?
Following are several steps for you to manually remove this ISCA 2012 fake program. If you are not confident enough, please backup your important data before making any changes to your computer.
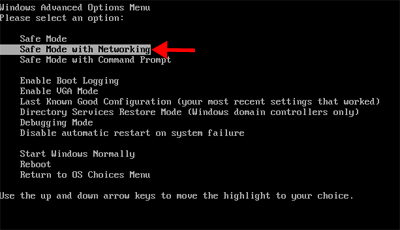
Step A: Reboot your infected computer and keep pressing F8 key on your keyboard. Use the arrow keys to highlight “Safe Mode with Networking” and press E/Enter.
Step B: Press Ctrl+Alt+Del keys together to open Windows Task Manager and then end related process [Information Security and Control Act (ISCA) 2012].

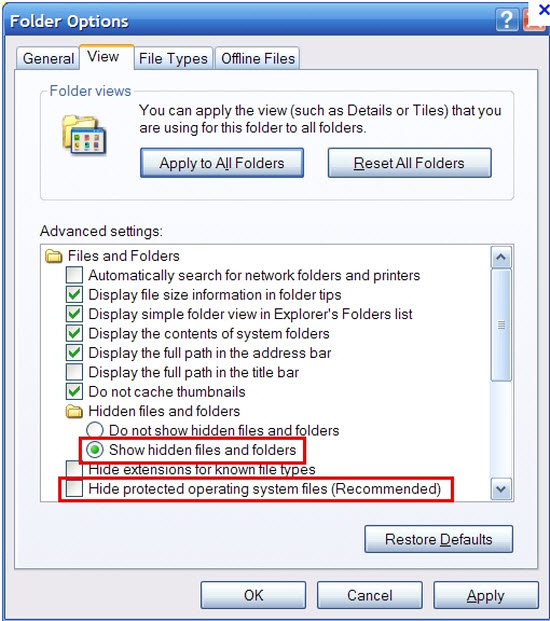
Step C: Open Control Panel from Start menu and go to Folder Options. Under View tab to tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then click OK.
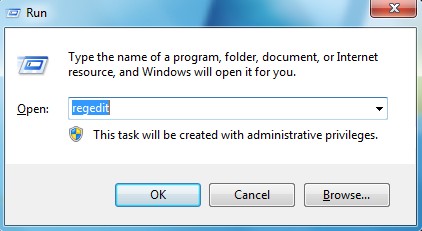
Step D: Press Windows+R keys to open the Run window and then type in regedit to open Registry Editor.
Step E: Find out and delete all these associating files and registry entries as below:
Go to %userprofile%\appdata\local\temp
The virus can have names other than “random.exe” but it should look like it doesn’t belong and should have a create date/time the same as a .class file if you sort by file mod/create time you’ll find it.
%AppData%\[ Information Security and Control Act (ISCA) 2012].exe
%Documents and Settings%\[UserName]\Application Data\[rnd].exe
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe(rnd)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[rnd].exe”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[rnd].exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\”Shell” = “[rnd].exe”
Video Guide On How to Remove Fake ISCA 2012 Scam:
To Sum-up:
According to researches and survey, this type of cyber issue has been quite popular in these days. Computer users from any countries can be infected by one of them like this Information Security and Control Act (ISCA) 2012 Scam. They may vary from names, looks and languages. But they all lock your computers because of some legal issues. In order to make you willing to pay, hackers try to make this fake program look as legit as possible from the name, appearance and related nation. Some people are believed to be too panic so they rushed to the payment via Ukash. But later they will regret and wonder how they can get their money back. It is impossible because they do not have any numbers to call or email addresses to write emails. The most important thing to do is to make sure that you don’t lose more to hackers. You can renew the information of your cards if you pay via your credit cards or other personal cards. Then take quick actions to get rid of this scam program so that it cannot collect your other personal information and bring other malware to damage your computer.
Note: Still find it difficult to manually get rid of this Information Security and Control Act program by following the above instructions? Have struggled enough with this info@online-cyber-police virus? You are welcome to contact YooSecurity Online Experts now to let them uninstall this Information Security and Control Act (ISCA) 2012 virus off your computer.
Published by Tony Shepherd & last updated on June 5, 2013 6:02 am










Leave a Reply
You must be logged in to post a comment.