Proxy.sh review here will help you learn more detail about Proxy.sh VPN, its features, functions, apps, software and network status and more. proxy.sh is a non-for-profit operation made up of experienced staffs who are located throughout the world but collaborate in a digital manner. Proxy.sh has a great VPN network in 57 countries and over 300 locations worldwide. They practice strict non-logging policy, that means Proxy.sh never keep logs of your personal data or share your online activities with other parties. you can completely trust Proxy.sh service. Besides, Proxy.sh is based in Republic of Seychelles where is a perfect jurisdiction for people require a higher level of privacy as no laws about data retention ask VPN service to comply with. Proxy.sh takes customer’s privacy more seriously.
Why you need Proxy.sh VPN? There are many ways to surf the Internet anonymously. In this paper, I will compare the advantages and disadvantages of some of the most common ways to surf the Internet anonymously. In addition to avoiding leaks of personal information, you can also get around increasingly strict walls. The advantage of VPN is the fast network speed; Can be Shared P2P download, Tor network advantage is high anonymity; Free; The combination of the two needs to consider the advantages and disadvantages of each other. Proxy.sh adopts the military-grade AES-256 encryption and multiple VPN protocol to increase more layers of security for customers. Proxy.sh designs their own client software called Safejumper which is a custom client and can connect to Proxy.sh strongly encrypted OpenVPN network. Safejumper works for Windows, Mac, iOS, Android and Linux. Proxy.sh provides unlimited bandwidth, unlimited server switching and unlimited data transfer. You also can experience competent features like SoftEther, CGIProxy Extra (DNS, TOR, SOCKS, etc.). Proxy.sh is powered by multi-hop technology which makes your identity more secure.
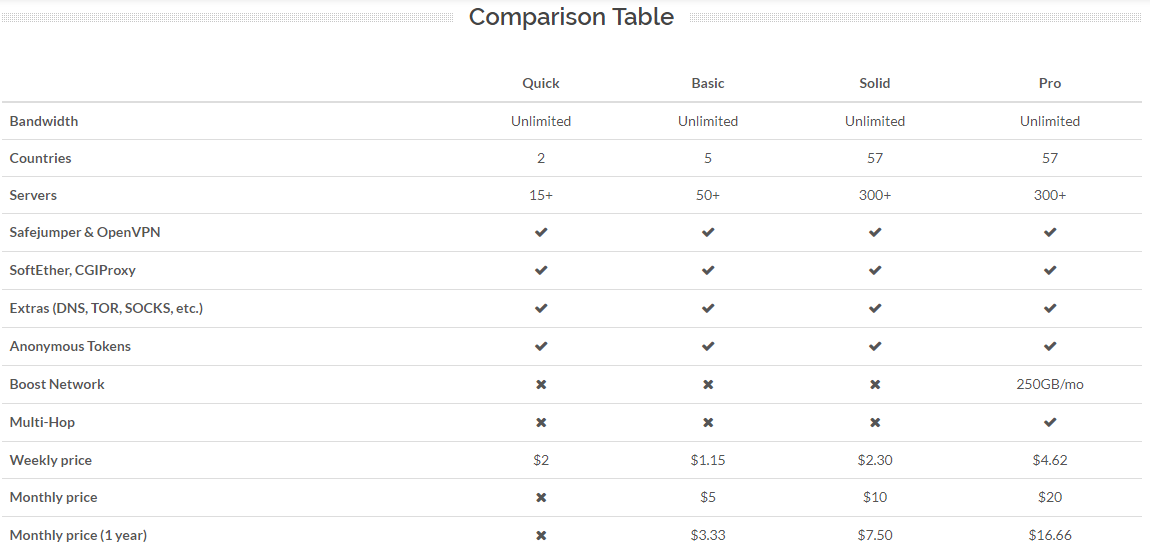
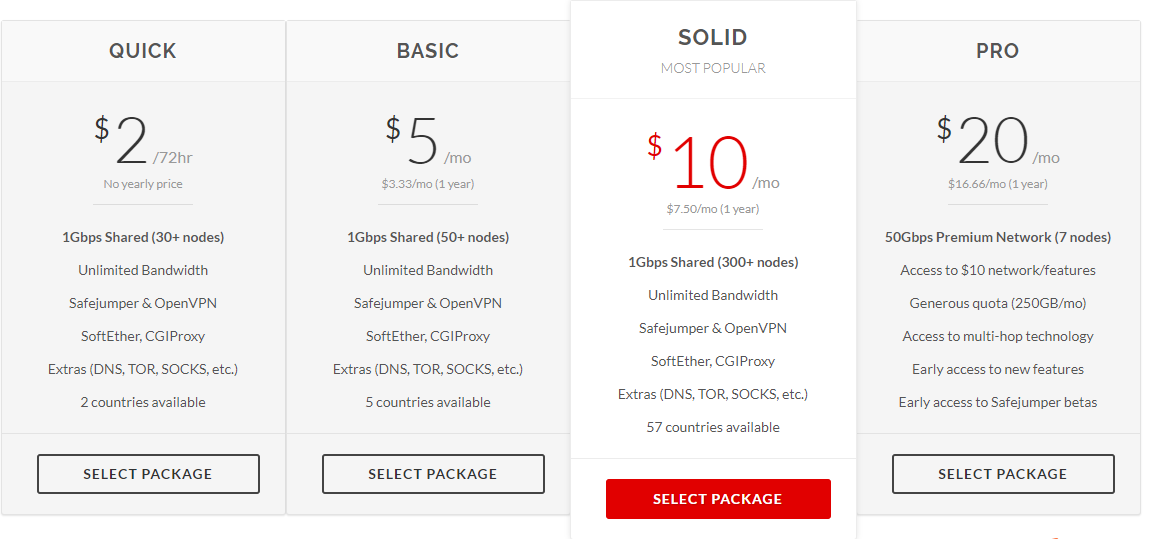
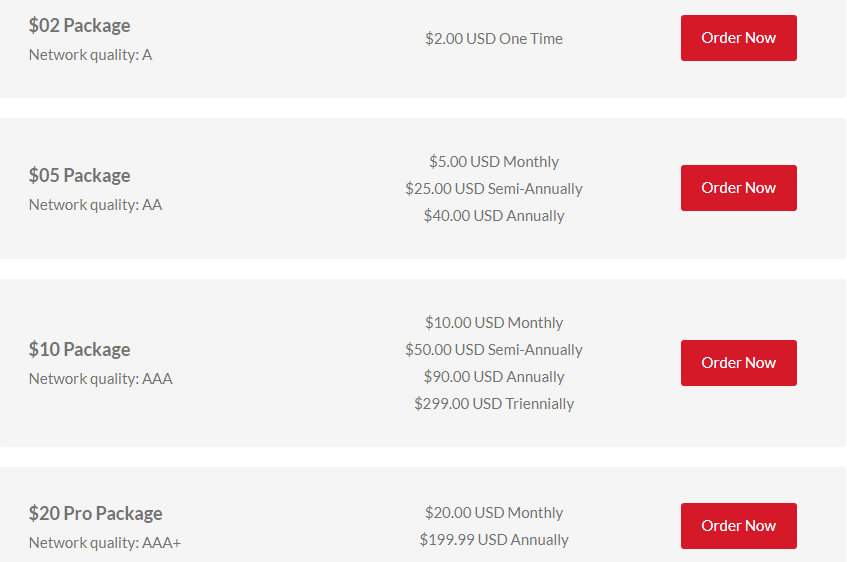
Proxy.sh Price Packages
Proxy.sh offers four different pricing packages: $2 USD for 72 hours, $5 USD, $10 USD and $20 USD per month.
The pricing packages make difference due to various qualities of bandwidth and a larger amount of available locations. For example, $10 Package includes many more locations & IPs than the $2 or $5 package. And the $20 package comes with access to the Boost network, which enables you to connect to VPN nodes established on the fastest lines of the Internet. Custom tailored solutionsare offered in any desired country in the world, for a quotable amount and for a minimum length of one year.
All packages include such primary and basic highlights as: Unlimited Bandwidth, Safejumper & OpenVPN, SoftEther, CGIProxy, Extras (DNS, TOR, SOCKS, etc.)
QUICK: $02 Package
- $2.00/72hr
$02 Package is specifically designed for people who want to get a quick protection or give a trial to Proxy.sh services. It allows you to connect to our 1Gbps nodes in two countries (United States & Netherlands).
BASIC: $05 Package
- $5.00USD Monthly
- $25.00USD Semi-Annually
- $40.00USD Annually
The $5 package is the best-selling standard. It gives you access to 1Gbps nodes in 5 countries (United States, Netherlands, Germany, France, United Kingdom).
SOLID: $10 Package
- $10.00USD Monthly
- $50.00USD Semi-Annually
- $90.00USD Annually
- $299.00USD Triennially
The $10 package is the best-effort package. It provides you with access to our entire network, made up of more than 50 countries and more than 300 1Gbps nodes.
PRO: $20 Package
- $20.00USD Monthly
- $199.99USD Annually
The $20 package is specifically built for demanding users and professionals. It provides access to the same network as the $10 package does, but it also gives you access to our Boost network. This network is made up of 50Gbps nodes. It will give you a fast and stable access to major Internet services and content delivery networks. It also comes with access to Proxy.sh Multi-Hop technology and SoftLayer Network (U.S. West, East, South, UK, Germany, Japan & Singapore)
What Sorts of Payment Method does Proxy.sh Accept?
Proxy.sh provides more than 100 different secure payment options from nearly anywhere in the world. These gateways are available either through PaymentWall, SafeCharge or OKPay. Here is the complete list:
Visa, Mastercard, American Express, Diners, Carte Bleue, DK, CartaSi, eNETS, PostePay, Fortumo, WebMoney, Sofort, Money Polo, W1, OOOPay Sberbank, Alfa Click, BTC-E, Mts, Beeline, Tele2, Exmo, Bancontact, WebMoney, PayPal, Cherry, Rbety, ePoints, DineroMail, MercadoPago, ClickandBuy, Mycard, Indomog, Pagseguro, Fanapay, RBK, Tutudo, Qiwi, Bank Transfer, iDeal, Poli, Dotpay, SanalPara, Postage, toditoCash, Mint, CashU, Ukash, WaveGame, Neosurf, GScash, Zong, Daopay, M1, Allopass, boxPay and Mikroodeme.
Some of these payment gateways are available only for specific locations, so you will have to select the country from which you’re going to pay before accessing the gateways, or attempt to connect from such a location using VPN.

Will Proxy.sh Log My Browsing Activities?
Proxy.sh provides a strongly-encrypted VPN network & online infrastructure that are all set to never log anything. And it runs most of all our services directly within RAM, which means a shutdown would erase all data. Proxy.sh does not keep any logs internally. Proxy.sh only logs your email address and purchase details like invoices linked to your email and your product details. But Proxy.sh does not log your activity like authentication or traffic on Proxy.sh’s proxy. They don’t even know whether you use the proxy or not. Your IP, location or anything about your browsing details will not be logged. Nevertheless, you’re kindly prompted that Proxy.sh does not process payments themselves. Proxy.sh offers anonymous tokens for a more secure purchase. But Proxy.sh’s payment gateways will log your IP, location and any information you provide to them. For details about Proxy.sh Privacy Policy:
We guarantee that we will use the information collected (see above lists) only for the following ends:
1) E-mail address is used to send subscription information and payment confirmations,
2) Payment data is used to manage client sign-ups, payments, and cancellations,
3) Google Analytics data is used to improve our website,
4) Apache web-server logs are regularly pruned and are created by the web-server,
5) Contact submissions and e-mails will be used for correspondence.
Proxy.sh does not collect or log any traffic or use of its proxy technologies including virtual private networks.
Where are the Servers of Proxy.sh Located?
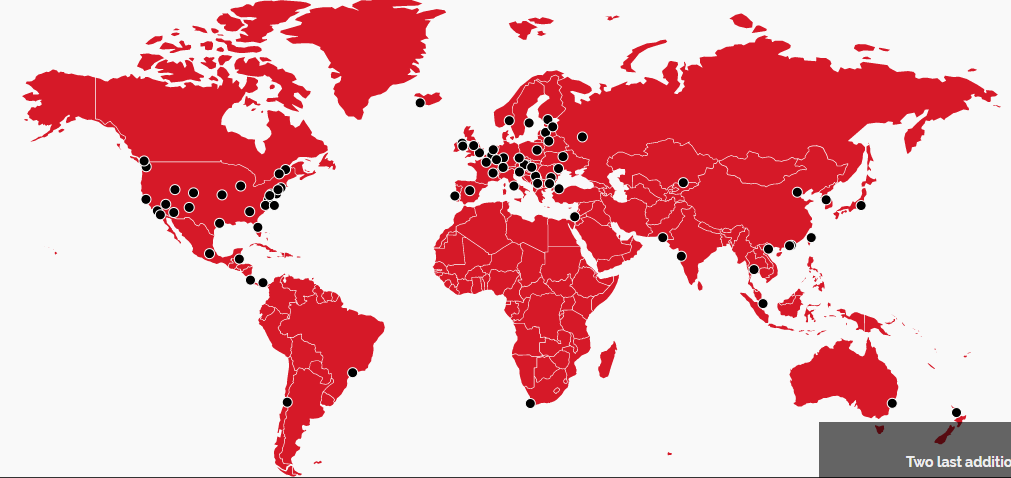
Proxy.sh builds strong and stable network and infrastructures across the globe. It provides real-time protocols & bandwidth availability for Proxy.sh servers in all locations and countries. Proxy.sh VPN provides more than 300 servers in 57+ countries and locations. Australia, Austria, Belgium, Belize, Germany, Japan, Singapore, United States, United Kingdom, Brazil, Bulgaria, Canada, Chile, China, Costa Rica, Czech Republic, Estonia, Finland, France, Hong Kong, Hungary, Iceland, India, Ireland, Isle of Man, Israel, Italy, Kosovo, Kyrgyzstan, Latvia, Lithuania, Luxembourg, Macau, Mexico, Moldova, Netherlands, New Zealand, Norway, Pakistan, Panama, Poland, Portugal, Romania, Russia, Slovakia, Slovenia, South Africa, South Korea, Spain, Sweden, Switzerland, Thailand, Turkey, Taiwan
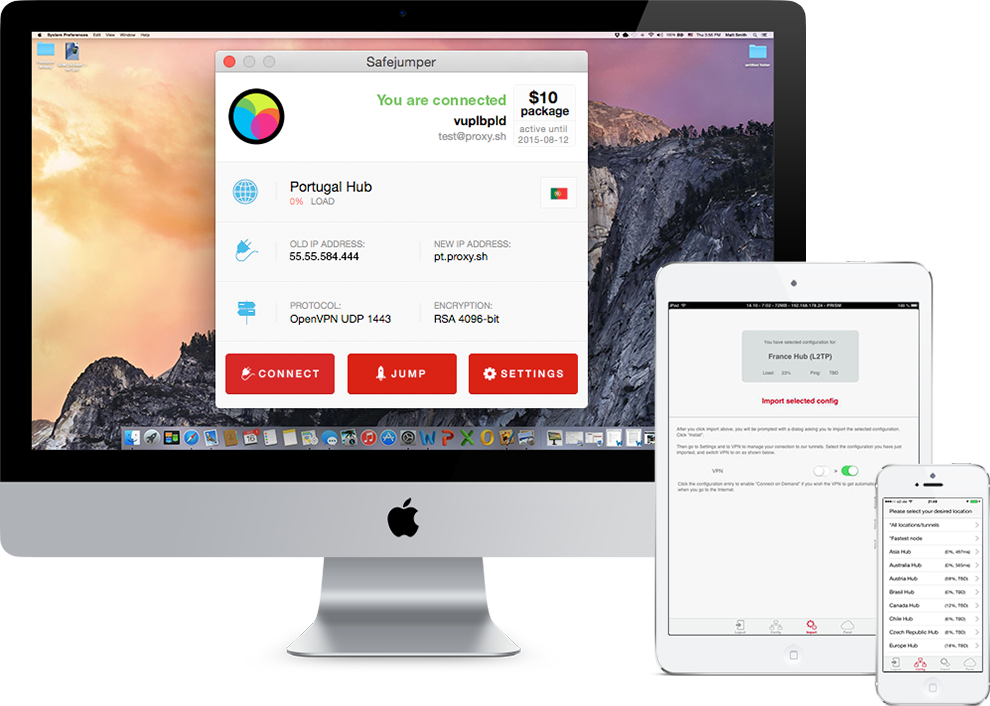
Saferjumper, the TOR-Powered VPN Client
Saferjumper is a custom application developed by Proxy.sh. Saferjumper is a Tor-powered VPN client. Safejumper lets you log into your VPN account and select various OpenVPN protocols, ports and locations in order to easily and securely connect to the Proxy.sh VPN network in few clicks or taps. The interface is designed to be stable, accessible and beautiful. Safejumper also allows you to tweak many network and account settings. It is a formidable companion to keep your Internet traffic strongly encrypted. Highlights of Saferjumper application:
- Compatible with five major OS
- Beautiful and stable
- Open source & built-in OpenVPN
- DNS leak fix and kill switch
- Compatible with ECC & ECC+XOR
- TOR’s obfsproxy (obfs2, obfs3, scramblesuit)
Saferjumper application works flawlessly with all popular systems including Windows, Mac OS X, Android, iOS and Linux. Safejumper is an OpenVPN client we have developed for you. It allows you to connect to our VPN network in few clicks or taps. Saferjumper is also easy to use. You just need to enter your proxy.sh VPN username and password, then log in and choose the country you wish to connect to. You also can select your favorite port and protocol, and click the Connect button. Safejumper is the best way to connect to any Proxy.sh VPN node with any OpenVPN port.
What Kinds of Protocols and Encryption Methods does Proxy.sh Support?
Proxy.sh provides OpenVPN with 256-bit AES/CBC, SHA-512 and 4096-bit RSA as cipher/hash/control. It also offers SoftEther, TOR, obfsproxy, ECC and XOR. Proxy.sh adopts the strong encryption method to increase more layers to protect user’s data and information. It allows you to enjoy complete privacy and security as well as internet freedom with a peace of mind.
- – OpenVPN-TCP: The cipher used by OpenVPN-TCP is CBC mode of ARS with encryption strength of 256bit, hash algorithm is 512bit SHA (SHA512). And the control channel is same TLSv1/SSLv3 DHE-RSA-AES256-SHA, 4096 bit RSA. Proxy.sh’s 4096 bit RSA key is changing every hour, preventing most advanced hackers and covert teams part of governmental agencies from breaking through.
- – OpenVPN-UDP: OpenVPN-UDP is equipped with the same encryption and security level as OpenVPN-TCP, but it works via UDP protocol which allows better speeds and bypasses more restrictions.
- – OpenVPN with ECC: It uses Diffie-Hellman initialized with 4096-bit key along with ECDH curve secp384r1 to encrypt. Its full control channel is made of TLSv1.2, cipher TLSv1/SSLv3 ECDHE-ECDSA-AES256-GCM-SHA384. Moreover, this protocol combines encryption cipher AES-256-CBC and the auth SHA512 to make the whole combination one of the strongest known to cryptographic research field. This ECC environment works well on port 465 (both UDP and TCP).
- – OpenVPN with ECC+XOR: Almost the same encryption level with ECC, it also uses Diffie-Hellman initialized with 4096-bit key along with ECDH curve secp384r1. Its full control channel is made of TLSv1.2, cipher TLSv1/SSLv3 ECDHE-ECDSA-AES256-GCM-SHA384 while associated with cipher encryption AES-256-CBC and the auth SHA512. Furthermore, this environment is supplemented with OpenVPN’s XOR scrambling option, which makes the whole combination probably the strongest known to cryptographic research field. “ECC + XOR” environment is provided on port 995 (both UDP and TCP).
- – OpenVPN with TOR’s obfsproxy: It makes use of our default encryption for OpenVPN along with obfsproxy on port 888 (both UDP and TCP). Proxy.sh offers obfs3, obfs2 and obfs3, obfs2 as obfsproxy standards.
- – PPTP: PPTP uses MPPE 128bit cipher with compression and MS-CHAPv2 authentication.
- – L2TP: L2TP is using IPSec for encryption with 256 bit key for encryption, 3DES/AES algorithm.
What Makes Proxy.sh Special and Excellent?
Prosy.sh is a solid VPN service that has strongly-encrypted network. Proxy.sh provides users with the highest standards in VPN cryptography. Proxy.sh’s standard OpenVPN is running 256-bit AES/CBC, SHA-512 and 4096-bit RSA as cipher/hash/control. Proxy.sh also provides ECC and Serpent as extra encryption methods, as well as XOR and TOR’s obfsproxy for scrambling your traffic. Proxy.sh also offers SoftEther, TOR, Obfsproxy, ECC and XOR, which all make Proxy.sh VPN power enough to access blocked websites, stream geo-restricted contents and circumvent the censorship. Proxy.sh has a strong ability to bypass the detection of any kind of censorship and anti-VPN tools.
1. Advanced Encryption Standard – Elliptic Curve Cryptography (ECC)
Proxy.sh offers a higher standard of encryption on its network. The higher encryption ECC has been as part of Proxy.sh VPN’s network encryption standards. ECC encryption standard is coupled with a 4096-bit Diffie-Hellman key, and the curve is ECDH secp384r1. The full control channel is made of TLSv1.2, cypher TLSv1/SSLv3 ECDHE-ECDSA-AES256-GCM-SHA384 while the associated cypher is AES-256-CBC and the auth SHA512, making the whole combination one of the strongest known to the cryptographic research field. This ECC environment is provided on port 465 (both UDP and TCP). It is easy to use ECC when you use Proxy.sh’s custom OpenVPN client called Safeiumper. Proxy.sh also provides OpenVPN with 256-bit AES/CBC, SHA-512 and 4096-bit RSA as cipher/hash/control.
2. Powerful SoftEther VPN
SoftEther is of the world’s most powerful and easy-to-use multi-protocol VPN software. SoftEther VPN has strong resistance against firewalls than ever. Built-in NAT-traversal penetrates your network admin’s troublesome firewall for overprotection. You can setup your own VPN server behind the firewall or NAT in your company, and you can reach to that VPN server in the corporate private network from your home or mobile place, without any modification of firewall settings. Any deep-packet inspection firewalls cannot detect SoftEther VPN’s transport packets as a VPN tunnel, because SoftEther VPN uses Ethernet over HTTPS for camouflage. SoftEther VPN has strong compatibility to today’s most popular VPN products among the world. It has the interoperability with OpenVPN, L2TP, IPsec, EtherIP, L2TPv3, Cisco VPN Routers and MS-SSTP VPN Clients. SoftEther VPN is the world’s only VPN software which supports SSL-VPN, OpenVPN, L2TP, EtherIP, L2TPv3 and IPsec, as a single VPN software.
3. TOR’s obfsproxy over OpenVPN
Proxy.sh not only uses the highest encryption standard to safeguard customers’ online activities and secure privacy from any third parties but also adopts unique obfuscation method TOR’s obfsproxy to let customers access any blocked contents easily. Obfsproxy is an obfuscation program that will scramble, or if you prefer, disguise your traffic to make it undetectable to firewalls and governmental monitors. It is what makes TOR users undetectable unless you monitor the exit nodes. Obfsproxy feature is easy to enable with proxy.sh client software Saferjumper. TOR’s obfsproxy is the best way to defeat the restrictions including internet censorship and geographical restriction that affect your network.
4. Strong ECC+XOR Combo Technology to Circumvent Censorship
Proxy.sh is also one of the rare VPN providers to combine ECC encryption with XOR obfuscation, which is a cutting-edging and advanced technology. ECC+XOR Combo technology lets you alter the “look and feel” of the traffic that goes between your devices and proxy.sh VPN network, making it more difficult for any external watchers such as network administrators or governmental agencies to detect you are behind a VPN. XOR patch adds obfuscation capability to OpenVPN, allowing it to bypass network traffic sensors which aim to detect usage of the protocol and log, throttle or block it. Proxy.sh provides XOR in exclusivity with ECC. The latter allows you to make sure your traffic will be next to impossible to decipher, while XOR allows you to make sure the third party cannot detect you are using OpenVPN. That’s why Proxy.sh is so strong and powerful that no third parties can break Proxy.sh tunnel.
5. Secure and Outstanding Multi-Hop technology
The Multi-Hop technology of Proxy.sh will let you connect to any VPN server as entry point, and then it will randomly route you through various VPN nodes of Proxy.sh across our network up to your selected exit point which will become your public IP. A self-configurable multi-hop VPN of Proxy.sh allows you to individually select the servers in the VPN chain. This means you can create new and unique VPN chains as often as you like. With this configuration, your true identity and IP address will be protected behind four different encrypted VPN servers. Every website you visit will only see the server details of the last hop in the VPN chain. You can simply enable the multi-hop configuration setting of Proxy.sh, and then dynamically add or remove VPN servers of Proxy.sh to the chain, directly in the application. A multi-hop VPN configuration of Proxy.sh is the best way to protect yourself against targeted monitoring and surveillance. VPN chains are also useful solutions for nation-wide surveillance and/or censorship. You can choose your entry point of the Proxy.sh VPN chain to be in your specific country (such as China), but then your exit point in a separate country. This setup helps to evade restrictions and national surveillance tactics.
Video Shows Proxy.sh Review
Top 10 + Best VPN Services Worldwide
| VPN Provider | Servers | Jurisdiction | # of Connections | Price(USD) | WebSite |
|---|---|---|---|---|---|
 |
ExpressVPN Review | British Virgin Islands | 3 | $6.67/Month |
Best Deals |
 |
NordVPN Review | Panama | 6 | $2.99/Month |
View Deals |
 |
PIA VPN Review | USA | 10 | $3.49/Month |
View Deals |
 |
IPVanish VPN Review | USA | 10 | $6.49/Month |
View Deals |
 |
VPNArea Review | Bulgaria | 6 | $4.18/Month |
View Deals |  |
Servers in 34+ countries. Unblocked in China. | Czechia | 5 | $4.88/Month |
View Deals |
 |
300+ Servers worldwide. | Seychelles | 3 | $3.33/Month |
View Deals |
View More Top 10 Best VPN Services Here »
Summary
After reading the Proxy.sh review you understand that Virtual private network (VPN) allows users to securely connect to the network in another place. A virtual channel is established between the computer and the VPN server. All network data is encrypted and transmitted through the VPN server to ensure the security of network data. The biggest difference between a VPN and an agent is that all network data is encrypted, including network connections for all applications installed on your computer, so the configuration of the VPN server is critical, depending on connection speed, location information, and security. Proxy.sh is a reliable and reputable VPN service that is used by millions of users all around the world due to its strong and remarkable features and technologies. Proxy.sh focuses on privacy. And it has a strict no logging policy. You can use Proxy.sh to stream your favorite contents from Netflix, BBC iPlayer, Hulu, HBO GO and more anywhere you want. Proxy.sh VPN has a high performance to bypass the internet censorship and geo-restrictions to access any websites you like. Proxy.sh is powered by different strong technologies which increase a layer of security. As a professional VPN provider of online proxy solution, Proxy.sh provides a wide range of proxy technologies such as VPN for a reasonably low amount of money. Proxy.sh nodes are located all around the world. They are incredibly discreet, fast and secure as well completely private. They allow users to hide their IP address (Internet identity) and location from unwanted sights without leaving traces either on the Internet. anyway, it is wise to use Proxy.sh VPN service.
Published by Tony Shepherd & last updated on April 10, 2019 7:57 am














Leave a Reply
You must be logged in to post a comment.