On my computer i have windows 7 and i downloaded google chrome, but whenever i go online it says Trojan:W32/DNSChanger was found by . Cyber cribbers resort to extreme measures to programme and improve various Trojan to create more and more invasion to personal computers. Trojan:W32/DNSChanger is such Trojan which has been spreading widely around the world.
Trojan:W32/DNSChanger is dangerous trojan horses Categorized as malware that detected by F-secure, Kaspersky or Symantec Security tool. It is the same stubborn as Win32:Sirefef-AO[Rtk]. It is extremely important to drop everything that you are doing and to concentrate entirely on removing Trojan:W32/DNSChanger from your machine. How big is the threat? And if you thought the virus threat was big, consider the incidence of spyware
infection. A 2010 study by America Online and the National Cyber-Security Alliance found that 82% of users’ PCs were infected by some form of spyware—
twice as many computers as were infected by viruses. Trojan:W32/DNSChanger is a pesky Trojan that will change the infected system’s Domain Name Server (DNS) settings, in order to divert traffic to unsolicited, and potentially illegal sites. If you tried to use anti-virus programs to scan your computer fully, then after a while during the scanning, the virus damage your internal network. Lately we got a few samples of this Trojan that were named ‘PayPal-2.5.200-MSWin32-x86-2005.exe’. This Trojan was programmed to change the DNS server name of a victim’s computer to 193.227.227.218 address. It seemed to be fine when you did a system restore to a point, but then infections will come back soon. That is crazy. The virus is hidden in the code of legitimate software programs—programs that have been infected, that is. When the host program is launched, the code for the virus is executed and the virus loads itself. Luckily, you can safely and absolutely get rid of Trojan:W32/DNSChanger here.
To save your computer, Live Chat with YooSecurity Expert Now, or you can follow the manual removal guide below to get your problem fixed. (For advanced computer users)
The effective way to deal with Trojan:W32/DNSChanger
Having problems with the virus? You found that the files had been renamed, but new ones had been generated after rebooted. Many victims ran the Kaspersky rescue disk, but it just scans the first few files and then aborts to desktop.The viruses blocked Windows Firewall service in your computer. Trojan:W32/DNSChanger is not in the range of common viruses. Such kind of virus can be unapprehended even you have an antivirus to protect your PC and effect your Network Traffic. So the really useful way to kill them is to remove the threats manually. Of course removal of such virus needs professional skills. And if you can’t remove them by yourself, we strongly recommend you to get YooCare/YooScurity for further help.
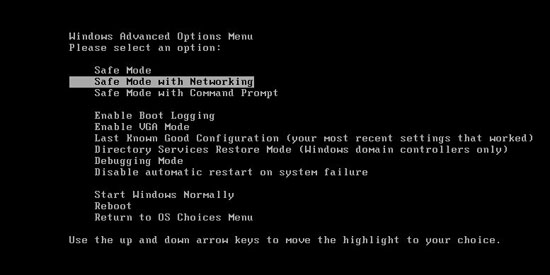
Guide to get in safe mode with networking:
Restart your computer. As your computer restarts but before Windows launches, tap “F8” key constantly. Use the arrow keys to highlight the “Safe Mode with Networking” option, and then press ENTER.
Basic steps to manually remove Trojan:W32/DNSChanger Virus
Press Ctrl+Alt+Del keys together and stop all processes of Trojan:W32/DNSChanger in the Windows Task Manager.
Open the Registry Editor, search and remove registry entries related to Trojan:W32/DNSChanger
All associated files of Trojan:W32/DNSChanger virus should be removed completely.
%systemroot%\system32\spool\prtprocs\w32x86\*.*
%windir%\ServiceProfiles\LocalService\AppData\Local\Temp\*.*
%windir%\ServiceProfiles\NetworkService\AppData\Local\Temp\*.*
Video Tutorial On How to Modify or Change Windows Registry:
Registry Entries That Generated By Trojan:W32/DNSChanger Virus
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce\
[HKLM\SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces]
“NameServer”
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{random}
DhcpNameServer = 85.255.xx.xxx,85.255.xxx.xxx
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces\{random}
NameServer = 85.255.xxx.133,85.255.xxx.xxx
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\
DhcpNameServer = 85.255.xxx.xxx,85.255.xxx.xxx
HKLM\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\
NameServer = 85.255.xxx.xxx,85.255.xxx.xxx
Note: If you couldn’t eliminate Trojan:W32/DNSChanger by yourself, please feel free to get YooSecurity 24/7 online support anytime you get stuck.
Published by Tony Shepherd & last updated on November 9, 2012 2:33 pm










Leave a Reply
You must be logged in to post a comment.