I harassed for some unknown merchants. I don’t know how did they know my contact and disturb my life? So I think I should protect my information all the time. Is it possible for ISP to peep my personal information? It would be a terrible thing if the data they sold about browsing history contained a significant proportion of browsing history that is atypical of real browsing. A terrible thing. Do you know how to protact my browsing histories from ISP?
How Could ISP Snoop on My Browsing Histories?
Do you think that ISP would be content with the monthly service fees that you pay them, but no, corporate greed is motivating them to try to monetize my private information. Your web browsing patterns contain a treasure trove of data, including your health concerns, shopping habits and visits to porn sites. ISPs can find out where you bank, your political views and sexual orientation simply based on the websites you visit. The fact that you’re looking at a website at all can also reveal when you’re at home and when you’re not. If you ask the ISPs, it’s about showing the user more relevant advertising. They argue that web browsing history and app usage should not count as “sensitive” information.
Many Countries are banning websites which you may use regularly, and private companies can often use your browsing data and forward it to the Government. Your ISP can easily track your data, and it isn’t illegal because they claim to do so for giving you better ads but they also may sneak out the information’s and no one can catch them. So, it is very important to make yourself a safe and secure browsing place where all your browsing history is enclosed without any breach of privacy. Protecting one’s internet usage should be invariably done due to terrorist groups and hacker groups waiting to feed on theinnocence of people. Some ways to protect the browsing history is by using a VPN provider.
What Kind of Personal Data do ISP Want?
ISP would be able to gather and sell data about your browsing history to marketers and other companies, including information on where customers are, as well as information about customers, such as financial or health status, and what people shop and search for. Protection and precaution are always better than being in a bad situation later on in life. We are in an age where everything is shared online, from pictures to important work details and we trust every network point blindly. We have logged into our bank accounts over the internet and have done transactions, and everything can be tracked by our Internet Service Providers (ISPs), they have a log of our browsing history which they can sell to anyone if they like. Even if we choose them very carefully and are sure that they are truth worthy, someone in the system can be faulty and leave you at risk. Several hackers and fishers are looming around the internet for your personal details and getting something of their benefit. Hackers can change your passwords or get into the business files that are precious to you, and they can do works in your name to harm you. We trust on our computer’s firewall and the different Anti-virus systems we buy, but technicians adapted to these barriers can easily breach them and reach for personal things.
To Protact your browsing histories to save the personal information, you need to encrypt all your internet traffic. Some websites (like the Guardian) are already encrypted – marked out with HTTPS at the beginning of the URL – but ISPs would still be able to see which websites you have visited, just not the individual pages. To mask all of your browsing behavior you can use a VPN service, and please note that may incurs a subscription cost, but it is no expensive.
Suggestion: If you don’t know how to access Hulu in China, you’re welcome to contact our Yoosecurity online technical team by clicking Start Live button bellow:

What is a VPN? Is VPN encryption legal?
• A VPN or Virtual Private Network is a very useful way to hide your personal information on the internet while it lets you browse through it. They ensure that your browsing is being done through a private, encapsulated network. They often do that by giving you a brand-new IP address than the one that your ISP provides; it will make you virtually untraceable and let you browse with ease.
• VPN’s use tools such as encryption, data encapsulation and tunneling protocols for birthing a safe horizon for the users. A VPN mainly conjures up a new IP address for the user which is situated far away from the actual location of the user which makes them invisible to the ISPs. Users can easily browse their internet and do banking transactions without getting scared of losing their credentials. For example – If someone is using google in the USA through a VPN then they may appear to be using it from a distant place like the UK.
• There are basically two types of VPN: Site-to-site VPN and Remote Access VPN. The type used mainly by home based users who access it on laptop or phone is Remote Access VPN.
• Another way VPN’s are divided into three families: 1. IPsec family that includes the Internet Protocol Security (IPsec) and Layer 2 Tunnelling Protocol (L2TP), 2. Point Tunneling Protocol (PPTP) family and 3. SLS family which includes Secure Sockets Layer (SSL) and Transport Layer Security (TSL) and Open VPN.
In multiple Western countries the power lobbies are pushing really hard to make encryption illegal since they cant snoop on people. China and Singapore however have legislation that permits them to disallow encryption and using it is a crime. Like in China you have to declare that you have encryption software in your computer, while only businesses can use encryption. Infect, VPN are not considered illegal in most countries and anyone can go ahead and start using a VPN service. The act of surfing through another IP is legal, and is something even the biggest companies in the world do all the time. VPNs help enable users working at home, on the road, or at a branch office to connect in a secure fashion to a remote corporate server using the Internet. From the users perspective, the VPN is a point-to-point connection between the user’s computer and a corporate server. The nature of the intermediate network, the Internet, is irrelevant to the user because it appears as if the data is being sent over a dedicated private link. When used for legal purposes, VPNs are not considered illegal in most countries and anyone can go ahead and start using a VPN service. The act of surfing through another IP is legal, and is something even the biggest companies in the world do all the time. If you however hide behind a VPN service to perform illegal activities, then you’re of course violating the law.
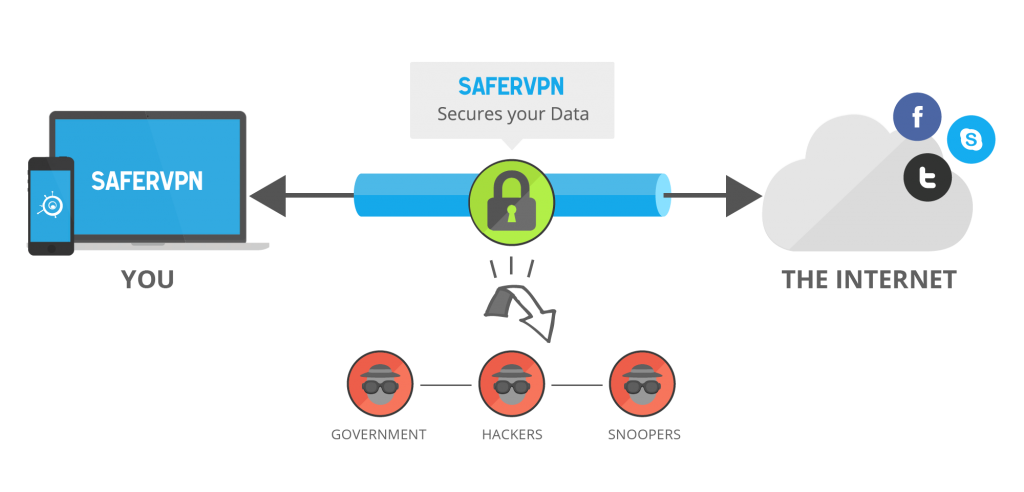
Why are VPN useful?
• It has hidden IP address, the VPN provides optimum security to the users, and they can browse anything and everything.
• It keeps one’s personal information hidden from the hackers and hinders unnecessary traffics that often arise in normal browsing.
• VPN’s provide unhindered security to the users, it is like a cloak which lets you talk and share personal items with ease. They do not record your search history which makes it safer for you from the ISPs.
• Cloaks the VOIP calls made.
How to choose a VPN provider?
Before choosing a provider one will need to think on the VPN Protocol for a smoother browsing. It mainly depends on the device being used, a laptop or desktop may run any protocol, but a mobile device can get choosy. An OpenVPN works well for a desktop based device, and a mobile device can run IPsec/L2TP protocols. PPTP is best avoided. L2TP/IPsec has heightened security, but it is slower.
VPN providers are either free or paid. We have to keep in mind that we want to protect our personal information, so choosing a reputable paid provider is the best thing to do. They charge an amount of money to let you browse the internet safely. They have higher security and many more locations options. You just have to see that how many devices you can run by using the same account.
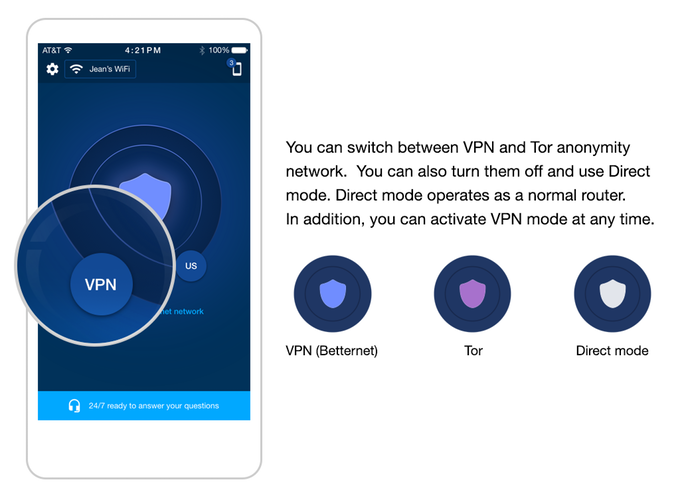
Using a VPN Provider
Step 1: You have to download the application of your VPN provider from online search or from atorrent if necessary. Download the VPN protocol for a smoother run.
Step 2: Create an account in the application and pay the amount securely. See to it that the payment gateway is not a scam one. This will help you log into the app always.
Step 3: Choose another location rather than yours and start browsing with ease.
Using Tor
Tor isn’t as comprehensive and easy as a VPN, but it is free. It is an anonymity software and can easily be installed on a desktop. It lets you browse with supreme anonymity and visit internet places where few can go. But you have to be logged into that software always to access the sites.
If you are using the above-mentioned applications to keep yourself and all the information personal then you will get good results and be safe. It is better to be precautious in this hungry world where we cannot trust anyone. ISPs are something that we have always had faith on because of us paying them, but other rich organizations pay them more, so nothing is safe. Be safe while browsing and keep an eye on scams or potential bad networks. It is better to use these and be safe and keep your computer browsing totally secured.
Warm prompt: If you don’t know which VPN service is the Best for you or how to set up VPN on Mac, computer, laptop, android smartphone, tablet, or iPhone &ipad device, you’re recommended to live chat with Our Online Expert for instant help! We will take care everything for you!
Published by Tony Shepherd & last updated on April 13, 2017 5:34 am










Leave a Reply
You must be logged in to post a comment.