ESET is a global cybersecurity solution provider that has over 30 years’ experience in protecting people from online threats. The company has been around since the early 1990s. Until now, ESET has protected more than 110 million users worldwide from spyware, malware and other internet threats. Is ESET a good antivirus software? How is it compared to other antivirus programs? Does it slow down PC performance? What are the features, benefits, and drawbacks of ESET antivirus? In this ESET review, we will be covering what this security product provides and how it performs so you can know whether it is value for money.
What’s ESET?

ESET is a pioneer in cyber security and it has been developing industry-leading IT security software and services for businesses and consumers worldwide for 30 years. The company is based in Bratislava, Slovakia, and has regional offices in North America, South America, Europe and Asia. It has come a long way since 1987. Until now, ESET has protected more than 110 million people in 202 countries and territories with its fastest, most effective and most proactive anti-virus and anti-spyware software solutions. ESET aims to build a safer technology environment for everyone to enjoy. So its products can eliminate viruses, spyware, adware, worms, trojans, rootkits and other malware before they attack your system. You will get peace of mind and stay away from ransomware and phishing for good with the protection of ESET.
ESET products include ESET NOD32 Antivirus, ESET Internet Security, ESET Smart Security Premium, ESET Cyber Security and Cyber Security Pro, as well as ESET Mobile Security (for Android platforms). It also provides Endpoint protection for Windows, Linux, Mac and Android, Anti-Theft, Encryption, and Parental Control, and there are some integration plugins for Kaseya RMM and LabTech RMM available. By utilizing unique ThreatSense technology, all ESET products deliver real-time protection from spyware, viruses and other threats while using very little memory and CPU resources. ESET is on the forefront of security innovation, delivering trusted protection to make the Internet safer for businesses and consumers. Whether you want to secure your computers and devices, protect your precious family pictures and data, or even keep your company know-how safe, ESET is here for help that gives you great detection rates, small footprint and centralized management.
ESET Products:
ESET products are made for you, your family, your company, and the people you care about. Whether you run a PC, Mac, Linux machine or Android device, you can protect them all with ESET Multi-Device Security pack. All its products are engineered with a multi-layered approach that protects users from spyware, malware, phishing and any other kind of viruses and threats. Check out the details here and choose the best product for you:
For Windows:
- ESET NOD32 Antivirus:
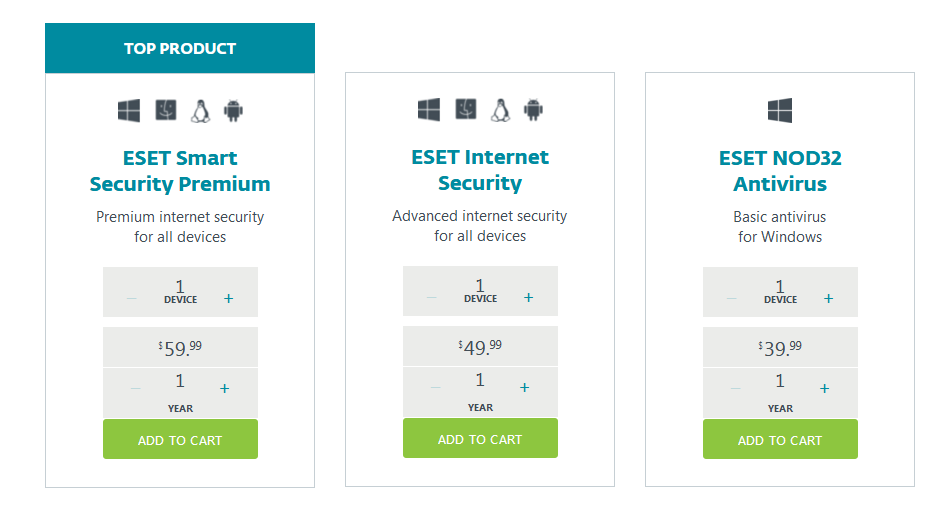
ESET NOD32 Antivirus is the entry-level version of ESET’s security services which is available for Windows only. The program includes all the basic features like Anti-Phishing, Antivirus and Antispyware, Cloud-powered scanning, Automatic Update, System Cleaner and more. All these features will ensure that you can defend against the latest malware infections, even including threats not yet named or fully recognized. With ESET NOD32 Antivirus you can browse the internet without slowdowns and enjoy gaming without distracting pop-ups. It is among the best antivirus available today, especially when it comes to performance and efficiency.
Price: NOD32 Antivirus starts at $39.99 a year for a single PC, with each additional PC license (up to five) adding $10 to the cost. Multi-year deals are also available, and all ESET antivirus programs offer a 30-day trial period.
- ESET Internet Security
The next step up, ESET Internet Security is a good antivirus suit with higher level of protection than ESET NOD32 Antivirus. However, it is also a Windows-only product. ESET Internet Security includes everything you can find in the ESET NOD32 Antivirus, plus a hardened browser that protects your financial data while you are shopping or banking online, and the Network Monitor utility that protects your network against hackers and intruders. It also contains a two-way firewall with network protection module capable of protecting vulnerable computers from network exploits, Anti-spam, Banking and payment protection, webcam protection, and parental control. On top of that, ESET Internet Security has an anti-theft module which helps locate stolen or missing devices.
Price: ESET Internet Security costs $49.99 yearly for a single device, with each additional PC license (up to 10) adding $10 to the cost. Multi-year deals are also available. You can save $65 or $130 if you sign up for 2 years or 3 years respectively. ESET also allows you to try the product free for 30 days before committing to a long-term subscription. During the free trial period, it doesn’t limit any features or require your credit card. Get advanced security for shopping and banking with ESET Internet Security now!
- ESET Smart Security Premium
The flagship antivirus product, ESET Smart Security Premium, lets you shop and bank safely, manage passwords and encrypt personal data like photos and account numbers. Compared to Internet Security’s offerings, it adds a password manager and file-level encryption, making it the best security solution to protect Windows device. This most feature-rich security product allows you to take advantage of all the protection that ESET has to offer and it doesn’t affect your PC performance. With the Smart Security Premium, you can protect your passwords, home network and even your online banking and payments using ESET’s special secure browser window, so there will be virtually no way someone can hack into your PC. You also can protect your webcam from misuse, check the security of your home Wi-Fi router, test your network-connected smart devices, manage your kids’ online adventures, and more.
Price: ESET Smart Security Premium runs on any system with Microsoft Windows 10, 8.1, 8, 7, Vista, and Microsoft Windows Home Server 2011. The price starts at $59.99, with additional device licenses at $10 each for up to 10 devices. Multi-year deals are also available.
For Mac:
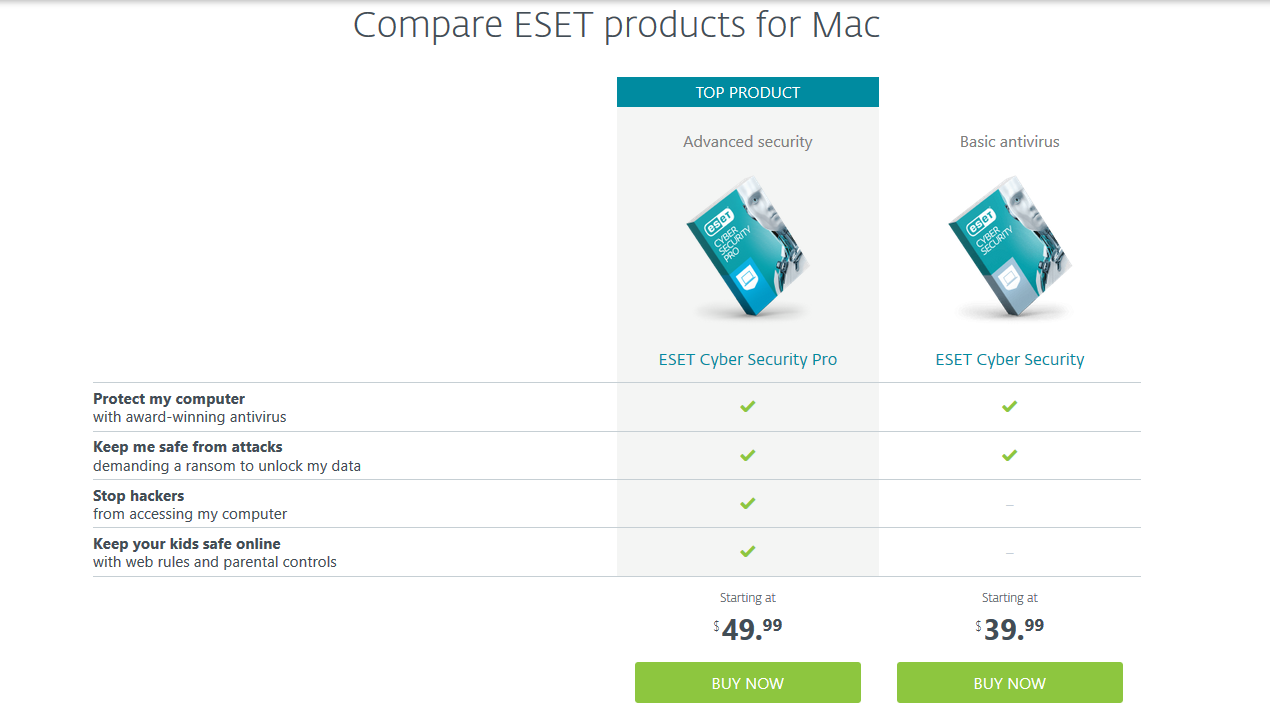
- ESET Cyber Security
ESET Cyber Security gives you fast, powerful anti-malware protection for your Mac, whether you’re surfing, working or gaming online. It can be enabled to keep you away from dangerous websites, especially those that may be employing phishing techniques in order to harvest your private information. With ESET Cyber Security you can enjoy safer technology with fast and powerful detection of Mac-based threats. You can protect your private data from being copied, while web and email scanning keeps you protected from various cyber threats. However, since it’s a basic product so it doesn’t contain much more advanced features like parental control and personal firewall. To take advantages of all ESET features on your Mac, you can consider ESET Cyber Security Pro instead.
Price: ESET Cyber Security for Mac is priced at $39.99 per year for a single Mac and $10 for each additional Mac up to five.
- ESET Cyber Security Pro
ESET Cyber Security Pro is a complete security solution produced from ESET’s long-term effort to combine maximum protection and minimal system footprint. It covers everything that ESET Cyber Security has and adds a personal firewall that prevents hackers from gaining access to your computer and keeps you invisible when you use public Wi-Fi. While most parents are concerned about their children’s computer use for a variety of reasons, the Pro version even adds a parental control that helps block unwanted internet content by categories or individual websites and keep your kids safe online. The user interface of this all-in-one security product is simple and streamlined. Get added layers of protection with ESET Cyber Security Pro now!
Pirce: As for the ESET Cyber Security Pro pricing, you pay $49.99 per year for a single ESET license. You can add more licenses for $10 each, up to a total of ten. Both products come with 30 days money back guarantee and include free U.S.-based support.
For Mobile:
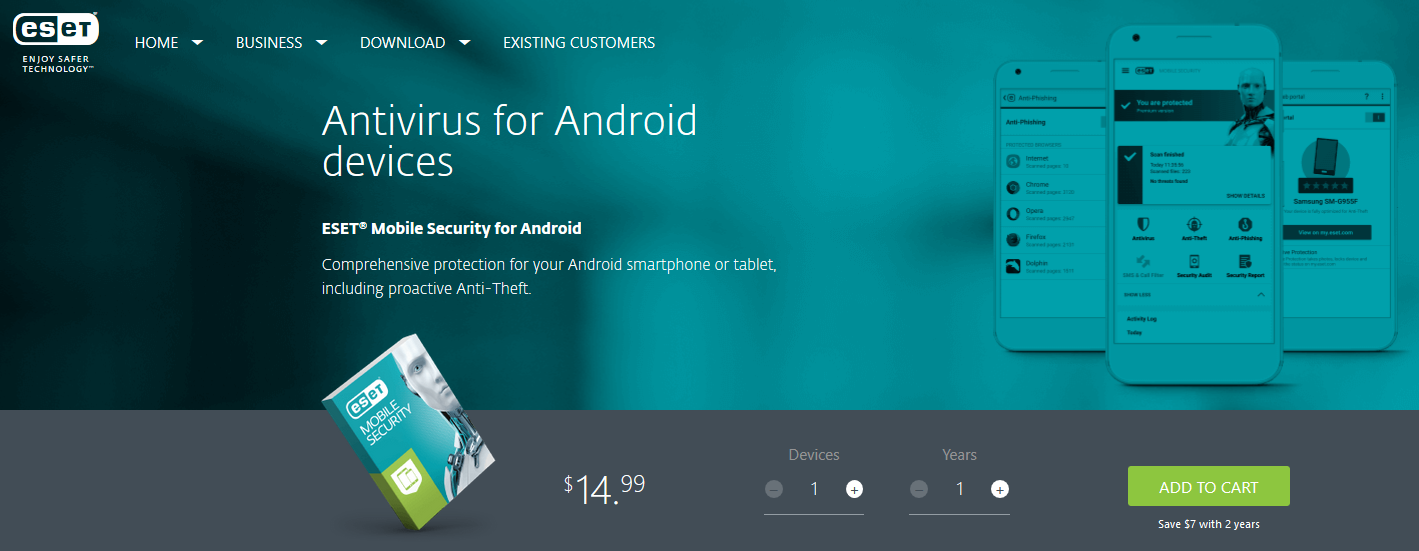
- ESET Mobile Security for Android
ESET Mobile Security is a “freemium” app that offers both free and premium levels of service to protect your Android tablet or smartphone against cybersecurity issues, including ransomware attacks. ESET Mobile Security can stop you against malware threats and phishing websites, and it even comes the ability to find your device and protect your valuable data in case your Android device is lost or stolen. The free version contains Antivirus, Real-Time Scanning, Security Report, Activity Log, Remote Lock, Remote Siren and Tablet Support while the premium version (starts with $14.99/year for one device) adds more advanced security features like App Lock, Anti-Phishing, Proactive Anti-Theft, Scheduled Scanning, Low Battery Alert, Automatic update of virus database, Connected Home Monitor and Security Audit. Get the complete protection on all your Android smartphones and tablets with ESET Mobile Security now!
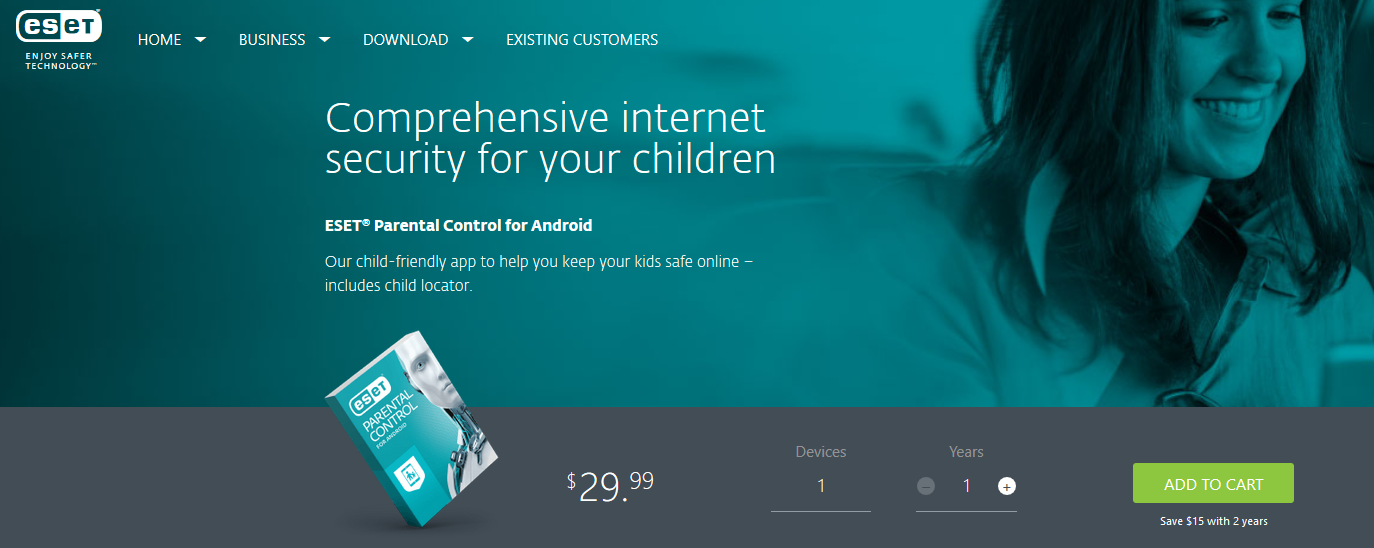
- ESET Parental Control for Android
Like several other antivirus-software companies, ESET has dipped its toes into the parental-control market. ESET Parental Control for Android is the best option for parents who want to have control over what websites their children visit, or what games and programs they use. This effective tool works well on Android device and it offers excellent protection and a moderate system-performance impact. With ESET Parental Control on your Android device, you can simply enter your child’s age, and categories such as gambling and pornography will be blocked automatically. The tool also allows you to set maximum usage time for the given day or to prevent access to certain categories during school or bed time. ESET Parental Control for Android follows the traditional freemium model. There’s a reasonable free tier that includes Web Guard Monitoring, Application Guard, Fun & Games Time Limits, Fun & Games Budget Limits and Basic Activity Reports. And the Premium Version which starts at $29.99/year for one device has all freemium features, plus Web Guard Filtering, Safe Search, Child Locator, Geofencing and Full Activity Reports. Use ESET Parental Control to protect your children against inappropriate online content and phishing web sites now!
Is ESET Worth a Try?
ESET is one of the biggest antivirus names in Europe and it has over 30 years of experience in helping people stop malicious threats and protecting their digital life. All its product get good scores in our hands-on tests and its collection of security components goes far beyond antivirus basics although in some cases it has a remarkably light system impact. ESET offers separate products for different platforms but unfortunately, ESET doesn’t offer official iOS support. So if you are looking for protection on your iPhone or iPad, obviously ESET is not for you. And for Windows users, ESET offers 3 different products namely ESET NOD32 Antivirus, ESET Internet Security and ESET Smart Security Premium. The 3 products start with essential malware protection and add features as the prices increase. It is worth mentioning that the anti-theft feature which helps you track down your laptop if it gets stolen is definitely a unique feature. Another different feature of ESET is the webcam security. If a rogue program takes control of your webcam ESET will notify you of such a violation of privacy. For Mac users, there are ESET Cyber Security and ESET Cyber Security Pro designed for them. The former provides comprehensive protection against a range of malware threats, such as viruses, ransomware, worms, Trojans, along with web browsing protection and free customer support while the latter adds a two-way firewall and parental controls more. If you are looking for a mobile parental control solution, ESET Parental Control is for you and it also offers ESET Mobile Security that gives comprehensive protection for android devices. Overall, ESET is worth a try but it still lacks some great tools such as virtual private network (VPN) client software, a file shredder and a system optimizer.
Published by Tony Shepherd & last updated on June 21, 2019 4:41 am










Leave a Reply
You must be logged in to post a comment.