I’m tired of dealing with Heuristic.BehavesLike.Win32.Suspicious.H, as my antivirus program told me that’s a Trojan, and this just happened to my computer after I click a link from my email to update my adobe player. Actually, there’s no adobe player at all, now I know some cyber criminals try to deceive innocent users to download the so-called useful programs, so they can transmit virus to them, and then take advantage of them. I very regret that I didn’t take it seriously in the first place, now my computer is kind of freeze sometime, it took forever for the cursor to respond I can’t open the WPS office to do my work right now, my antivirus program didn’t do anything about it, so I decide to turn for help from internet before I go to a local shop to have my PC fixed, so please help me!
Brief Introduction to Heuristic.BehavesLike.Win32.Suspicious.H
Heuristic.BehavesLike.Win32.Suspicious.H is a Trojan and a broad classification used by many antivirus programs to engine a file that appears to have Trojan-like features or behavior for software that exhibits suspicious behavior categorized as potentially malicious. It will bypass the permission of computer users to download and installs other programs on the sly. This could include the installation of additional malware or malware components to an affected computer!
When Heuristic.BehavesLike.Win32.Suspicious.H intruded into a computer system, the affected computer will gradually suffered from a bad condition as time goes by. The most noticeable infection for a victim to see is that, the infected one will be running very slow, and it’s not about how many years the infected computer have been used. Some of the programs will not be able to turn on. Let me explain how was that happen to a infected one. After installed, this Trojan contains malicious or potentially unwanted software which downloads and installs on the affected system. Normally, it will lead the innocent user to some vicious website, and then forcibly or silently download many malicious programs into the computer without consent from the user. Since these programs installed, most of them will be activated in the background without letting victim know, then the computer cpu usage will be highly occupied by them. Even though there’s no program running on the system, the computer still stuck in poor performance, the backdoor may then be used by remote attackers to upload and install further malicious or potentially unwanted software on the system.
The infection from different users may vary because of the generic nature of this detection. The Heuristic.BehavesLike.Win32.Suspicious.H infections may often install themselves by copying their executable to the Windows or Windows system folders, and then modifying the registry to run this file at each system start or restart.
There are several ways for this Trojan to spread on the internet; the cyber criminals always make use of computer users’ vulnerabilities. For example, users can be tricked into using non-malicious programs, such as Web browsers, to unknowingly perform malicious actions, such as downloading malware. Some otherwise harmless programs may have flaws that malware or attackers can exploit to perform malicious actions. Also, malicious websites, or legitimate websites that have been hacked, can infect your machine through exploit kits that could also let your computer suffer from Trojan as well. And there is a very normal way for bad guy to trick innocent people is spam email containing infected attachments or links to malicious websites. Some people may be fooled by the fake and tempting information; it will announce that it is from a shipping company like DHL or FedEx or for instance a bogus update for Adobe Flash Player or another piece of software. The email tells you that they tried to deliver a package to you, but failed for some reason. Sometimes the emails claim to be notifications of a shipment you have made. Anyway, if you can’t restrain yourself to open it, then that’s highly chance for you to face a annoying situation. After you have a certain understanding from this Heuristic.BehavesLike.Win32.Suspicious.H, you properly won’t sit back and watch if it happen to your PC.
The properties of Infected Computer
-Can escape from antivirus programs and slightly install on computers
-Can report a new infection to its inventor
-Can make your computer run slowly which properly lead your computer to blue screen
-Can download unnecessary files or malware automatically, which could harm your computer system
-Can receive orders from a remote cyber criminal
-Can be taken use by hackers with your private information and data for unlawful act
NOTE: If any of these properties show on your PC, your computer probably got infected with Heuristic.BehavesLike.Win32.Suspicious.H. And believe or not, this will cause you more problem later and may ruin your system. If you don’t have sufficient knowledge of computer, Please contact YooSecurity Online PC Experts to remove this virus for you.
At present, no perfect antivirus program can detect this Trojan or delete it efficiently. The most effective way is to remove it manually. The following instructions need quite level of computer expertise, for manual removal is a complicated and difficult process. If you don’t have sufficient knowledge of computer, please contact with YooSecurity online support now!
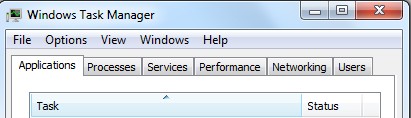
Step A: Open Windows Task Manager to end process related to this Trojan infection. To do that, press Ctrl+Alt+Del keys at the same time to pull up Window Task Manager; go to Processes tab on top and scroll down the list to find.
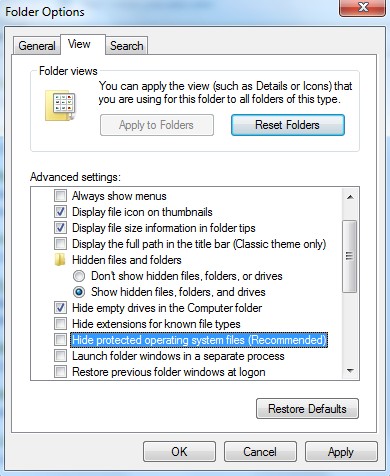
Step B: Open Control Panel from Start menu and search for Folder Options. Go to Folder Options window, under View tab, tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then click OK.
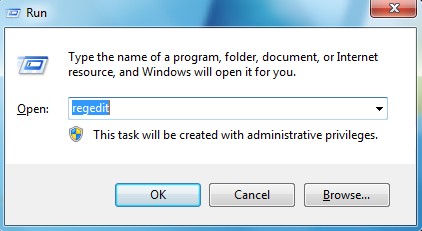
Step C: Press Windows+R keys to pull up Run box and type in regedit to open Registry Editor.
Step D: Delete all these associated files and registry entries with Heuristic.BehavesLike.Win32.Suspicious.H from Registry Editor. The registry files are listed randomly. Besides, you need to delete the infection files of the redirect virus from your system files to prevent it from coming back. Those files are named randomly also but may be different on different operating systems.
Video on How to Modify or Change Windows Registry Safely:
Conclusion:
However, if you don’t want to see your computer suffer from Heuristic.BehavesLike.Win32.Suspicious.H Trojan, or even let your private info or data get used by bad guys, then you’d better take preventive measures, such as be careful when downloading programs and pay more attention from this virus. If your computer still suffer from this Trojan one way or another, do not freak out, I may tell you it need remove manually, it’s the most effective way to get rid of this kind of Trojan or other similar kind of virus from your PC. Manual removal will be the best way to get rid of the Heuristic.BehavesLike.Win32.Suspicious.H from Computer.
Suggestion: To follow removal guide that mentioned above, a level of computer knowledge is needed. Still can’t get out of this virus? Contact online experts for help now! 
Published by Tony Shepherd & last updated on October 4, 2014 1:04 pm










Leave a Reply
You must be logged in to post a comment.